1. Version Information
Using Access Control Lists to Control Access to Unified Products
2. Document Purpose & History
Multi-Layered Protection
The UCP and eMG80 are embedded devices. The ACL should be considered the last line of defence against malicious users and attackers. The ACL should be configured and used with suitable edge firewall rules. For example, a port forward of port 5060 with no source IP designation is effectively writing a rule allowing SIP hackers to attempt to gain access to the Unified Product, and is almost certainly not the firewall rule you want.
ACL Default Action
There are a number of default actions. These are summarised on the help page of ACL in the Web Admin.
< Default ACL Action >
1. Deny All: The only packets with a source address and protocol in ACL will be permitted. Other packets with different protocol or source address will be rejected.
[Exception] The SIP signal packet is not affected to this rule. So the SIP packet will be passed and processed with successful at application level.
2. Allow All: Vice versa of ‘Deny All’
3. Deny List: The protocol packets with a source address in ACL will be rejected. Other same protocol packets without a source address in ACL will be permitted. Filtering is not applied to the different protocol type or out of port range.
4. Allow List: Vice versa of ‘Deny List’
The Deny All action, is clearly not suitable for protecting against SIP. Due to this limitation, this document focusses on the Allow List.
Allow List Packet Processing
The Allow List will allow a packet to pass to the Unified Application using the following:
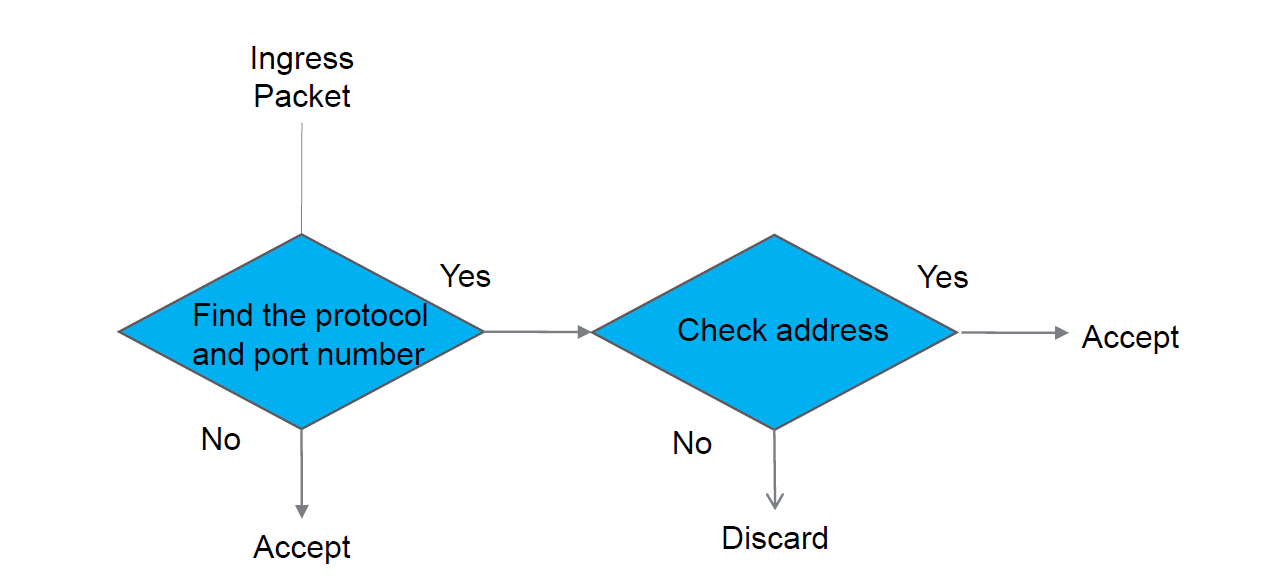
Unlike Deny All, the Allow List is passive until we write a rule. An empty list will restrict nothing. When we want to restrict a port we must list all valid sources. You can use a port in more than one row to designate more than one valid source.
Preparing to Write or Modify ACL Rules
Before modifying the ACL, particularly if you are modifying the rules for the web administration, make sure to take a backup of the system. In the very worst case you can default the system, and restore the old database, or load it from USB using the System Attendant.
Ensure you have serial port access, or telnet access to port 5003, and have set a remote password to access the command line to disable ACL, should you enter erroneous rules and lock yourself out. It is somewhat harder to do this with Allow Lists than Deny All.
Refer to Knowledge Base Article “Removing ACL Setting When locked out of the System”, to turn ACL off using the serial port or port 5003.
Allow List Rules
You must specify a protocol and port when writing Allow List rules. The rules will tend to have a direction of “Destination”, as we are filtering traffic based on the port it is trying to connect.
An example set of rules are:
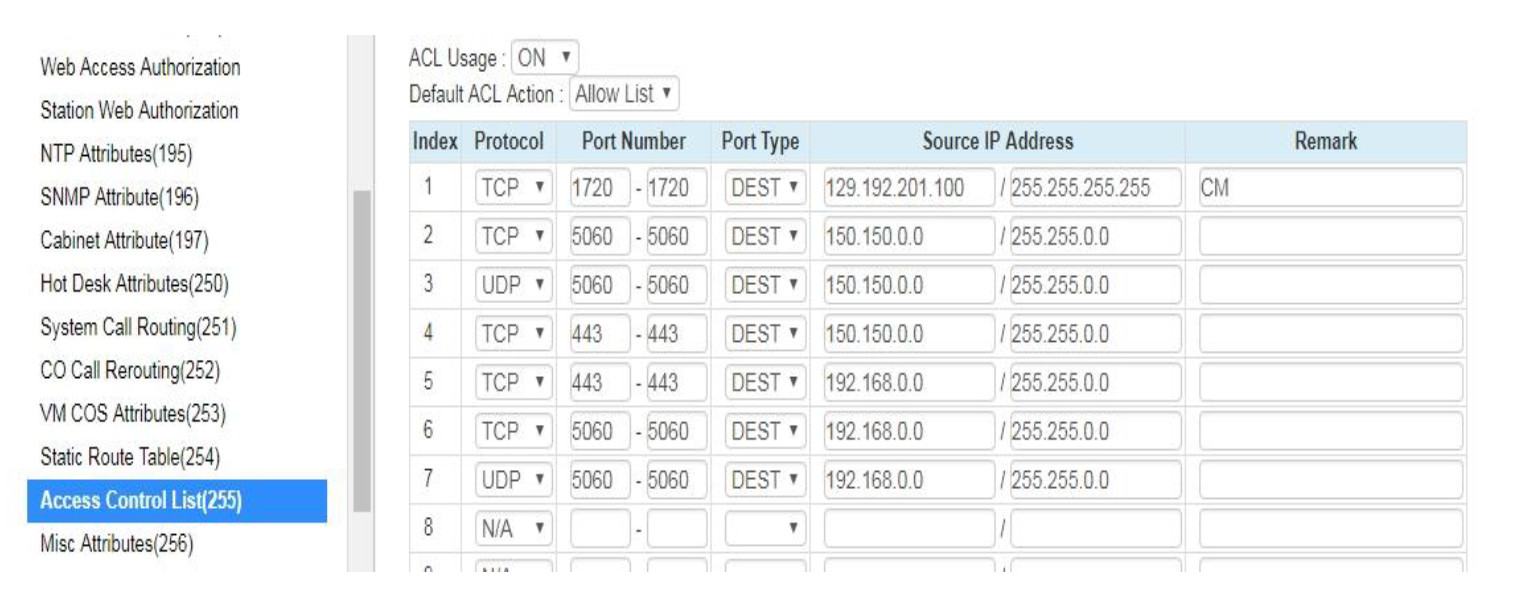
The above ruleset demonstrates some basic techniques.
- Rule 1 protects port 1720, the H.323 and inter-site networking port. In this rule set, only the IP address 129.192.201.100 may connect to TCP port 1720. The subnet mask i 255.255.255.255 specifies a single IP address, rather than a subnet.
- Rule 2 protects the TCP SIP port. If you are writing ACL rules to control access to SIP services, do not forget that the UCP listens for connections on 3 ports, not just udp port 5060.
The ports are specified in SIP Common Attributes (210), options 3, 4 and 5.
Normally the SIP carrier uses UDP port 5060, so the TCP and the TLS (SIPS) port, do not need to be, and are not exposed externally.
- The UDP port 5060 version of rule 2. Rules (2) and (3) allow IP addresses 150.150.xx to access SIP.
- TCP port 443 is the default port for the Web Administration portal, 443 is the default https port. This rule allows 150.150.x.x to access the web administration and user portal.
- This row also allows IP addresses 192.168.x.x to access TCP port 443, in addition to those specified in rule (4).
- This row allows IP addresses 192.168.x.x to access SIP TCP port 5060, in addition to the IP addresses allowed in rule (2).
- This row allows IP addresses 192.168.x.x to access SIP USP port 5060, in addition to the IP addresses allowed in rule (3).
Shutting Down an Unused a Service
Some network environment require services to shutdown all unused services on a server. You cannot stop services on the Unified Product Sometimes you wish to “turn off” a service. For example tcp port 7878, although protected by TLS and username/password authentication, allows calls to be initiated. The port is used by Clickcall and UCS.
If these products are not in use, you might want to “shutdown the service”. We can mimick this using allow lists on ACL. Consider the following rule.
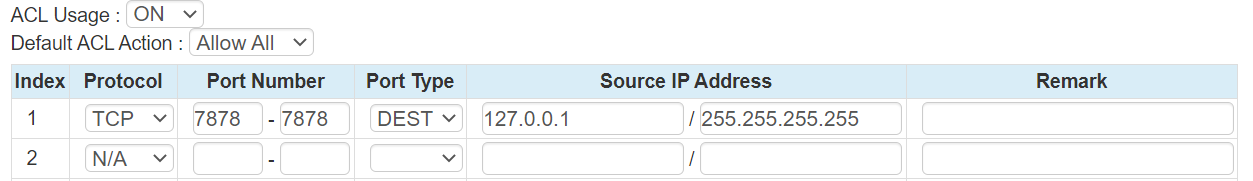
We can see this applies to TCP port 7878, used by UCS and Clickcall. The Source IP Address of 127.0.0.1 / 255.255.255.255 is the loopback IP address. The loopback IP address is only used on a device, it means the device itself, because of this, you should never see 127.0.0.1 on any network. This rule allows on applications running on the UCP itself to talk to port 7878. No network device may communicate with the service listening on TCP port 7878.
Applying the ACL or Changes
The ACL rules can be saved and can be applied. Saving the ACL rules, saves the rules but does not immediately apply the rules. Use Apply after save to make the rules as listed the rules being enforced.
Regards,
Simon Smith
Tech support
Pragma – Unified Technology
t: +44 1903927101 e: 480900 simon.smith@wearepragma.co.uk w: www.wearepragma.co.uk
Follow us @wearepragma | LinkedIn | Check out our YouTube channel
Please use these links to access technical resources, some require login:
TeamSupport Ticket System:Click Here| Knowledge Base:Click Here
Software Library: Click Here| Documents and Manuals:Click Here
Training Courses & Webinars: Click Here| Tech Support Policy:Click Here
“

Leave A Comment